This probably seems like a stupid question, implying that cyber-attacks are like people trying to break into your workplace in the middle of night and a well-aimed torch beam holding them in the spotlight and ultimately scaring them off. And yet this is exactly how security monitoring systems work.
Cyber-attacks come in all shapes and sizes from the next generation of Slow Death Denial of Service (DoS) attacks that can bring down practically any website from outside the network, to the sneaky Advanced Persistent Threats (APT) that worm their way onto the network and can sit dormant for months before waking up to cause havoc from the inside…
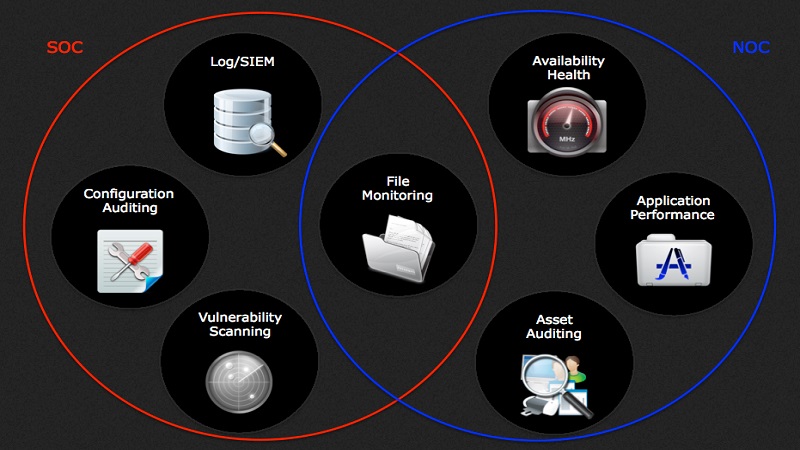
Each Monitoring System is a Spotlight
Although attacks can come in many forms, the protective monitoring systems used to identify them are still limited to only being able to monitor one or two data types each.
For example, Security Information and Event Management (SIEM) systems monitor log data and can let you know that something has happened – which may or may not be a cause for concern – but if you wanted to identify specifically what happened, such as to check the configuration files of devices to identify changes that have been made, you need a different monitoring system because log systems do not audit configurations and config systems do not monitor logs.
This same problems extends into availability, file integrity, behavioural anomaly detection, vulnerability, asset, database, application monitoring and many more.
In fact, it is not unusual for a large company to have a number of different monitoring systems or more – each “shining a spotlight” on one aspect of the information security infrastructure.
This problem is finally being acknowledged
Even the monitoring companies themselves own up to the problem.
Amit Yoran, president of RSA Security (vendor of the EnVision SIEM product) admitted that “logs are simply not enough” and “comprehensive visibility is the base block for truly insightful analytics and scoping out incidents correctly” in the opening keynote speech of the largest information security conference in the world, held in San Francisco in February 2016.
But is not the only recent admission. AlienVault’s new White Paper on Unified Security Management begins by admitting: “The dirty little secret in the SIEM industry is that most SIEM solutions have a shelf life of approximately 18-24 months before organisations give up and begin to look for another SIEM solution.”
In reality, hackers have little or no difficulty navigating the ‘dark patches’ of a network ensuring that their attacks are all but invisible to each individual monitoring system, and it is left to the skill, knowledge and an experienced eye of the hardworking security analyst to try to spot these attacks.
It doesn’t have to be this way
The UK-based independent software vendor called Pervade, voted one of the UK’s Most Innovative Cyber Security Companies in a techUK competition held at Infosecurity Europe in London last year, launched the world’s first security monitoring system after two years of self-funded development; which is capable of correlating, gathering and reporting on ALL DATA TYPES in a single configurable system.
In a recent filmed interview for The Telegraph, CTO Jonathan Davies said: “By bringing all data types into a single system we have brought an end to this crazy spotlight-based monitoring and finally turned the floodlights on. Current and future attacks are going to find it very hard to hide from detection when their every move can be correlated and displayed on a single screen”.
If you believe that you may have gaps between your monitoring spotlights or dark patches in your infrastructure contact Jonathan and the team at Pervade Software for an insight into the next generation of protective monitoring.
E: jidavies@pervade-software.com
T: +44 (0)29 2064 7632