Pervade Software: Where would you shine a spotlight on cyber-attacks?
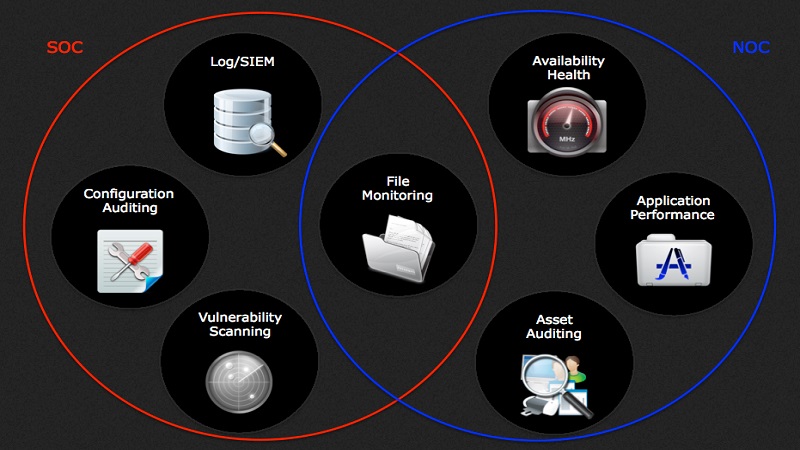
This probably seems like a stupid question, implying that cyber-attacks are like people trying to break into your workplace in the middle of night and a well-aimed torch beam holding them in the spotlight and ultimately scaring them off. And yet this is exactly how security monitoring systems work. Cyber-attacks come in all shapes and sizes from the next generation of Slow Death Denial […]
Industry Spotlight: “It’s one of a kind and nothing like this has ever been done before”…
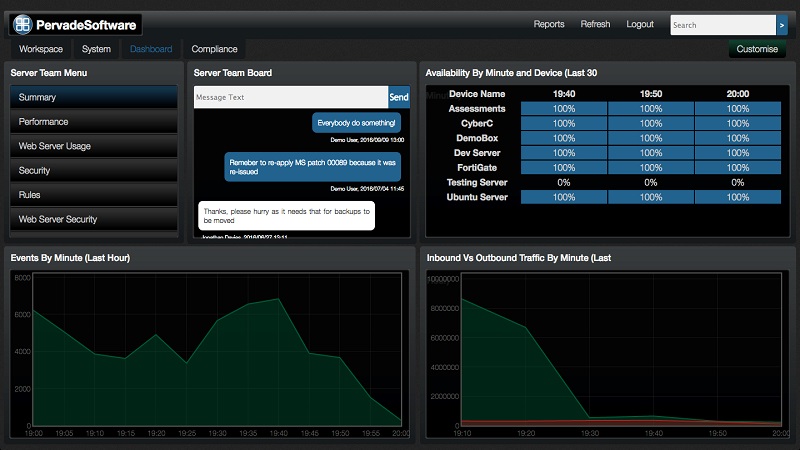
Used in more than 80 countries, Pervade Software‘s solutions are leveraged by a wide audience of private and public sector clients, as well as partners ranging from independent consultants to global managed security service providers. Here, John Davies, managing director, discusses the company’s premium position in the global and UK marketplace, the challenges it faces when approaching potential clients and keeping up […]

