Technological advances pushing mobile video surveillance growth

The Global Mobile Video Surveillance Market was worth $2.35bn in 2022 and expected to reach $4.25bn by 2028, equivalent to a CAGR of 8.79% over the forecast period. With rising crime rates in both digital and physical worlds, the importance of location and asset surveillance has increased. Mobile video surveillance, which facilitate real-time monitoring and […]
CIOs – Heading for a new direction

Three years ago, CIOs were winning plaudits from the rest of the c-suite for the way the IT team scrambled to deliver a digital workplace within a matter of days. Now, however, the shine has faded badly. While traditional IT performance measures may point to great system uptime, utilisation and performance, the human digital experience […]
Who foots the bill in the event of a data breach?

Data breach is almost inevitable – which means it is vital that companies and their Managed Services Providers (MSPs) understand exactly who is responsible and who bears the financial brunt. But recent research reveals that both companies and MSPs are disturbingly unclear about their legal and financial obligations. Contracts are ambiguous and the risks of […]
IT Governance: 31.5m records breached in December 2022

In its latest analysis of data breaches and cyber attacks across the world, IT Governance has identified 78 publicly disclosed security incidents in December – resulting in 31,586,757 compromised records. Compared to November 2022, we can see a slight decline, where we identified 95 publicly disclosed security incidents and 32,051,144 compromised records. Alan Calder, Founder […]
Respecting data privacy rights through data encryption

John Michael, CEO at iStorage considers the need for increased privacy in relation to sensitive information and looks at the methods and mechanisms to ensure high levels of data security… Data privacy should be a top priority for all organisations. As systems and services increasingly move into the cloud as part of the digital transformation […]
60% of firms optimistic about cloud sovereignty innovation and collaboration

Cloud sovereignty is increasingly becoming a priority for organizations looking for secure, innovative, and scalable solutions to manage their data, according to Capgemini Research Institute’s latest report, “The journey to cloud sovereignty: Assessing cloud potential to drive transformation and build trust”. The report finds that cloud sovereignty adoption is primarily driven by regulation and organizations’ […]
Web threats ‘increased by over 130%’ at the end of 2021
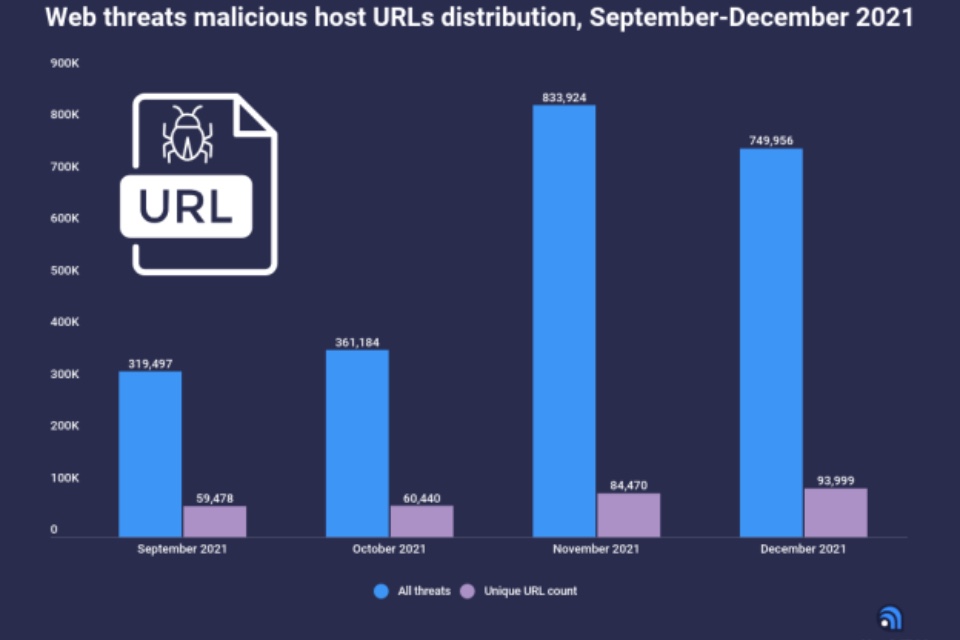
According to the data presented by Atlas VPN, web threats have increased by 133% in November and December of 2021, compared to September and October. In addition, JavaScript downloaders and crypto miners were the most active web threats at the end of 2021. Web threats affect everyone and every device that is connected to the internet. […]
Three reasons the security industry is protecting the wrong thing

Why is it that the security industry talks about network security, but data breaches? It’s clear that something needs to change, and according to Paul German, CEO, Certes Networks, the change is simple. For too long now, organisations have been focusing on protecting their network, when in fact they should have been protecting their data. Paul outlines three […]
Impact of COVID-19 on physical security market revealed

A new report delivers what it calls the best estimate of the global market for physical security products going forward to 2025, based on two scenarios. In March 2020, The World Health Organization declared COVID-19 a global pandemic. Within a few weeks, it was clear that the pandemic was highly likely to cause the world’s […]
Demand for datacentre solutions set to rebound post-COVID

A return to pre-COVID levels of confidence regarding future demand for datacentres was an encouraging finding from the latest independent industry survey, which captures the views of over 3,000 senior datacentre professionals across Europe, including owners, operators, developers, consultants and end users. The Winter Report 2020/21, now in its 13th Year is undertaken by independent research house IX […]

