Don’t worry if you missed last week’s BlueFort and Forcepoint webinar ‘Uncover The Hidden Risks Of Shadow IT’ – You can watch the entire session again online!
The number of people working remotely has tripled recently. This shift in culture comes a shift in risk. Staff may have the best intentions when they use personal devices, new software and emerging applications to get their jobs done more efficiently – but the use of unapproved IT resources creates vulnerabilities and opens you up to security breaches.
In the 20 minute webinar, BlueFort Security‘s Pre-Sales Director Josh Neame and Forcepoint‘s Senior Sales Engineer Alistair Mills discuss the risks and rewards of shadow IT.
“We’re seeing a lot more interest in issues surrounding shadow IT because of the current COVID-19 climate – a lot more companies are moving their IT into the cloud, which means there’s been a resurgence in shadow IT and a corresponding need for the relevant tools for monitoring,” said Neame.
“The pandemic means we’ve seen a rush to digital services as organisations look to plug the physical gaps created by their workforces operating remotely,” said Mills. “There’s suddenly a huge number of collaboration platforms being used, both for internal comms and with external partners – as employees we expect our IT and security departments to allow us to use those solutions in order to help get our jobs done.”
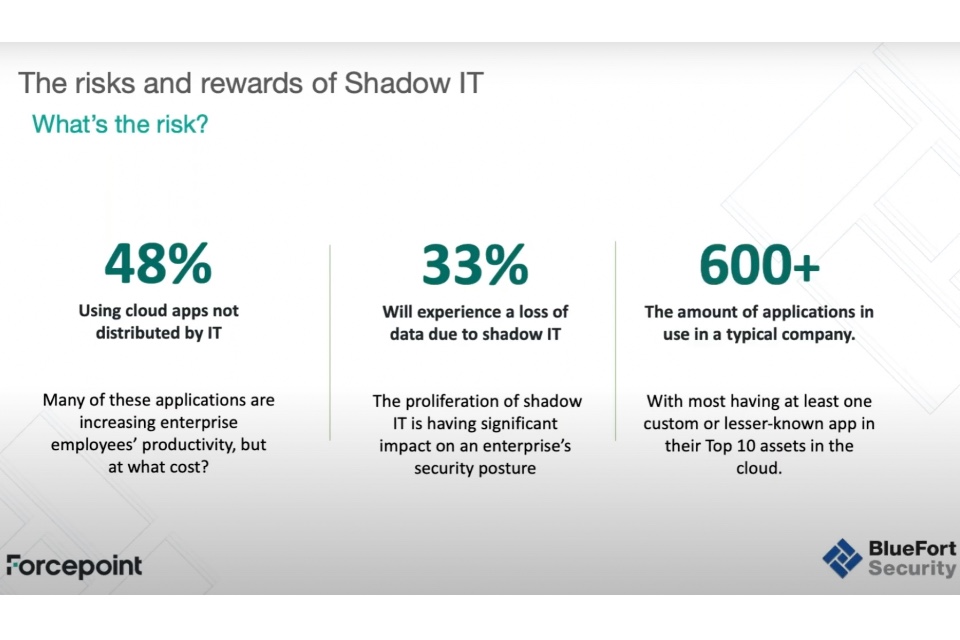
In the session, Mills and Neame drill down into the issues surrounding shadow IT, which they define as: ‘IT solutions and systems created and applied inside companies and organisations without their authorisation‘. Specifically, they look at:
- The threats and potential rewards Shadow IT creates for your business
- Identifying which employees are using unapproved IT resources and which resources are being used
- Getting full visibility of the extent of Shadow IT within your company
- Taking control of your IT landscape
Watch the entire session again here: